Server Key Management - S/Notify for Jira
Using an S/Notify release before version 4.0? Then please refer to Earlier Versions for the appropriate documentation.
Under this section, the private PGP keys and S/MIME certificates of the Jira server are managed. They are used for decrypting incoming emails as well as for signing outgoing emails.
For this, you will find the following configuration options:
Server Key Management
If you neither have set up Jira to process incoming email, nor want outgoing email to get signed, then there is no need to provide a server key store, and you can leave this section empty.
Note that, if you have configured Jira to use multiple email addresses, the key store must either hold multiple keys or certificates for them, or the keys or certificates must be issued for multiple email addresses.
This section has two tabs each displaying one of the two different encryption methods.
S/MIME
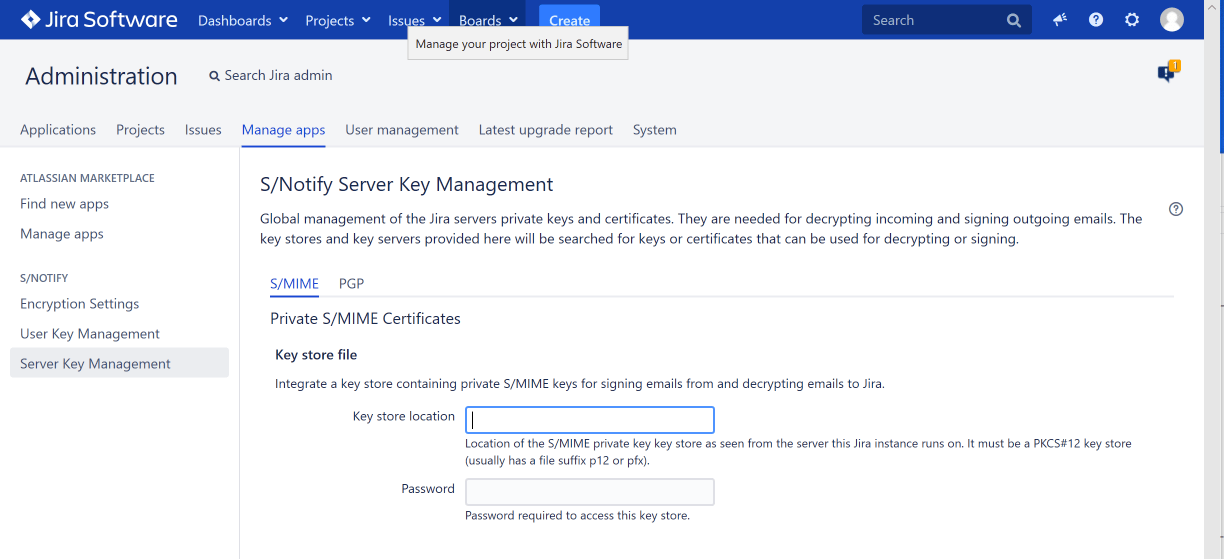
Private S/MIME Certificates
In this section, you can optionally provide a key store containing the private certificates to be used for S/MIME email decryption and email signing.
If outgoing emails are to be signed, the server key store should also contain the (public) intermediate certificates, so they can be included in the signature.
Key store location
Provide path and file name of the certificate keystore, as seen from the server your Jira instance runs on. The key store must be in PKCS#12 format. The file suffix of such key stores is usually p12 or pfx.
Password
Enter the password required to access the S/MIME key store. That is the keyword used to create the the key store.
For details on how the stored password ist protected, see below.
PGP
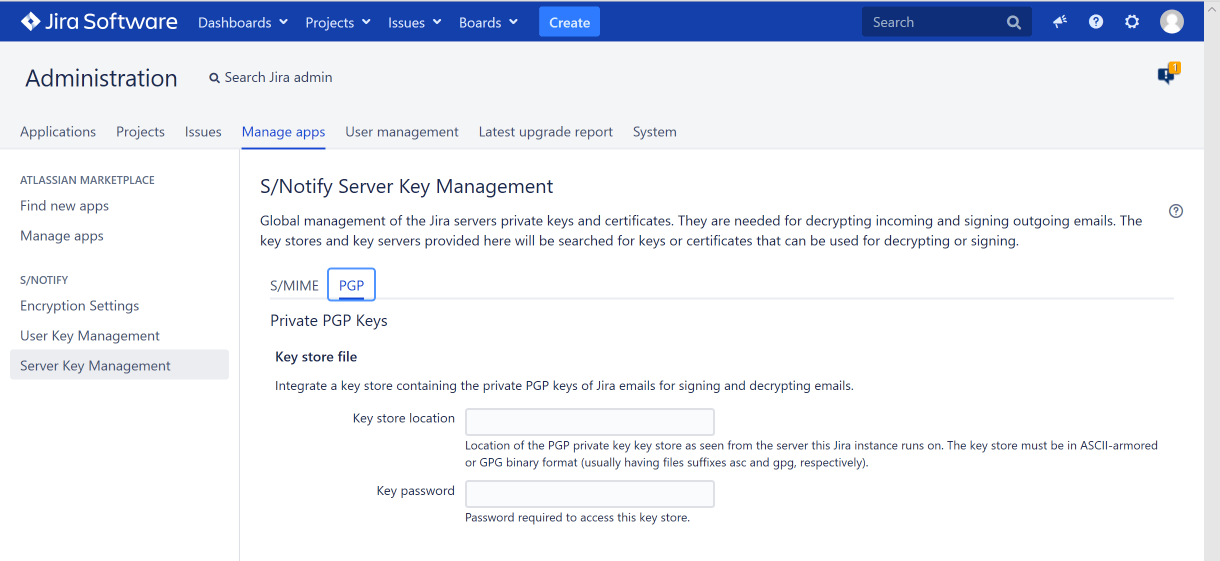
Private PGP Keys
In this section, you can optionally provide a key store containing the private keys to be used for PGP email decryption and email signing.
Key store location
Provide path and file name of the certificate keystore, as seen from the server your Jira instance runs on. The key store must be in ASCII-armored or GPG binary format. The file suffixes of such key stores (also called key rings) are usually asc and gpg, respectively.
Password
Enter the password required to access the private PGP keys in the key store. That is the passphrase used to store the secret keys in the key store. When using multiple private keys, all of them must be protected by the same passphrase.
For details on how the stored password ist protected, see below.
Password protection
The passwords are stored in the database in encrypted format and used only internally. They cannot be reproduced by any Jira user or administrator. However, since encryption of passwords alone cannot be considered fully safe, appropriate access control of your database is a prerequisite to achieve adequate protection.
Verify Settings
Before or after updating the settings, it is possible to run a verification.
The verification uses the given email address (new from S/Notify 4.1) and searches all configured sources for matching S/MIME certificates and PGP keys. If you leave the email address field empty, the default email address configured under Outgoing Mail, as well as email addresses configured in Project Settings > Notifications will be checked against.
The result of the search will be listed, including any error that may have been encountered. This allows to easily check for configuration problems that can the cause for issues with decrypting or verifying incoming emails, or with signing outgoing emails.
Expire Cache
When this button is hit, all cached S/MIME certificates and PGP keys are marked expired. Consequently, next time when an S/MIME certificate or PGP key is needed for encryption, they will be retrieved freshly from the key store or key server. Use this when you want S/Notify to reload certificates and keys.
If you update any of the configuration options, this also expires the cache, so after that, all certificates and keys will be retrieved again.