(3.x) S/Notify Overview
The following is intended to provide you with an overview of how S/Notify is integrated in Atlassian Jira, Atlassian Confluence and Atlassian Bitbucket, and how it works to support email encryption.
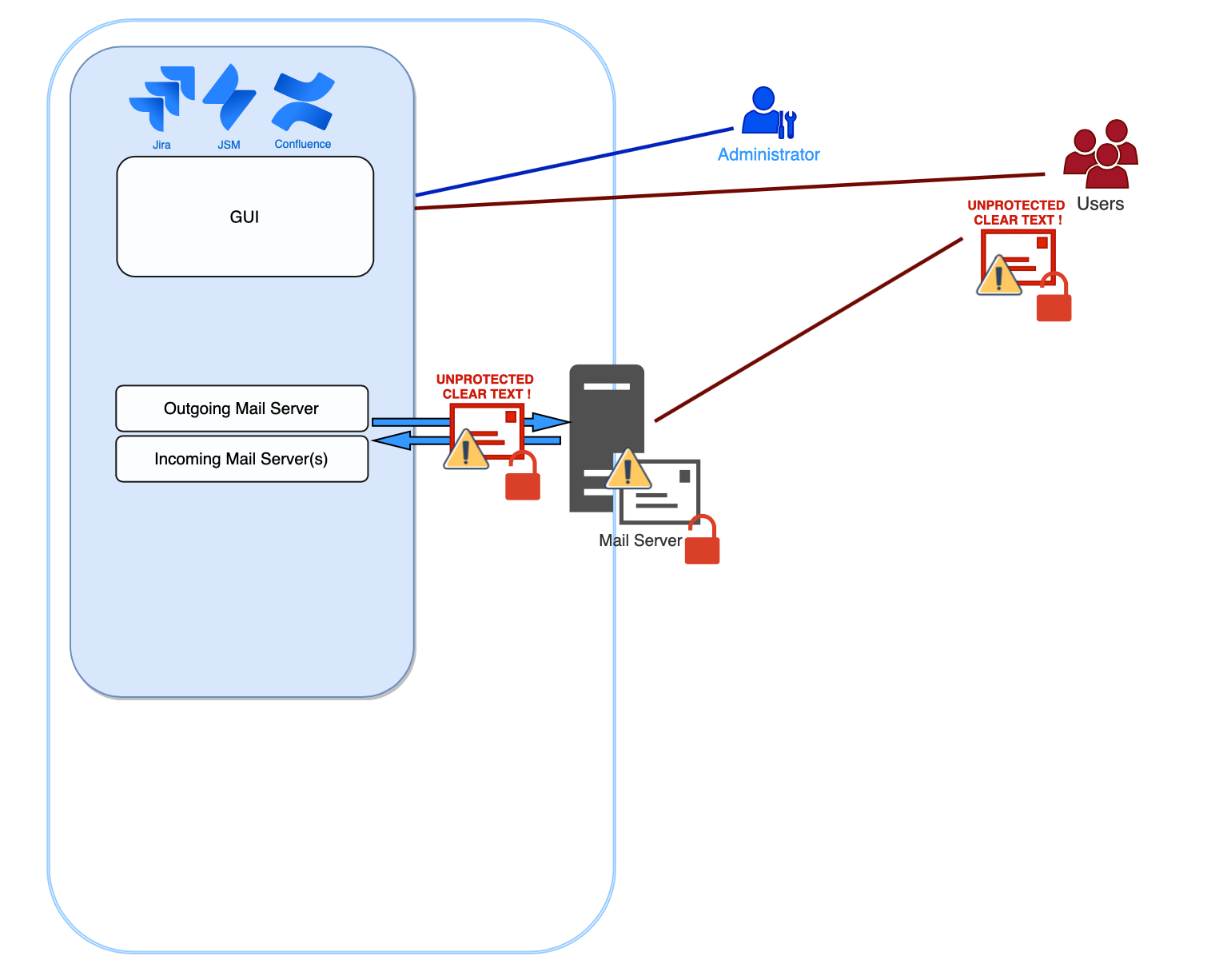
Standard Unprotected
The following diagram illustrates a standard Jira, Confluence or Bitbucket instance that does not protect outgoing or incoming emails. Even with TLS transport encryption between mail servers, there is no real end-to-end encryption. Emails stored on mail servers are in clear text, thus not protected in case of an attack or data leak. Note that emails are unprotected also on the users' computers.
End-to-end Protection with S/Notify
Outbound Email
With the S/Notify Email Encryption app installed, outgoing email can be easily encrypted. Through either S/MIME or PGP encryption, real end-to-end encryption is applied. Even in case of a mail server attack or data leak, the emails can never be decrypted without the recipient’s private key.
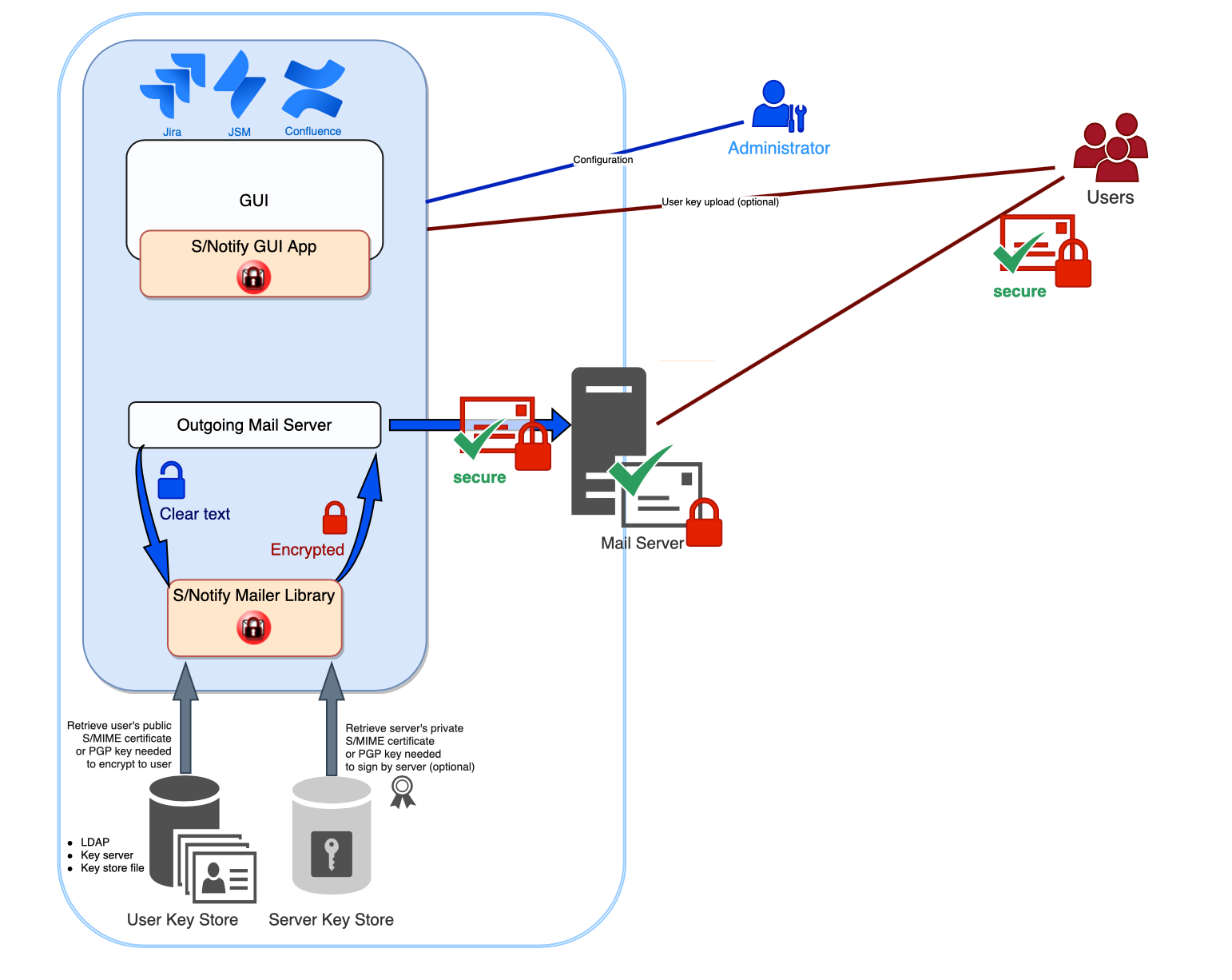
The users' S/MIME certificates or PGP keys can be retrieved from LDAP servers, PGP key servers, PKCS#7 key bundles, or GPG key rings, whatever fits best in the given environment.
In addition to encryption, it is possible to sign all outgoing emails to prove their authenticity to the recipients.
Inbound Email
In Jira and its variations, including Jira Service Management, S/Notify allows for protection of inbound email through encryption. Incoming S/MIME or PGP encrypted email is automatically decrypted.
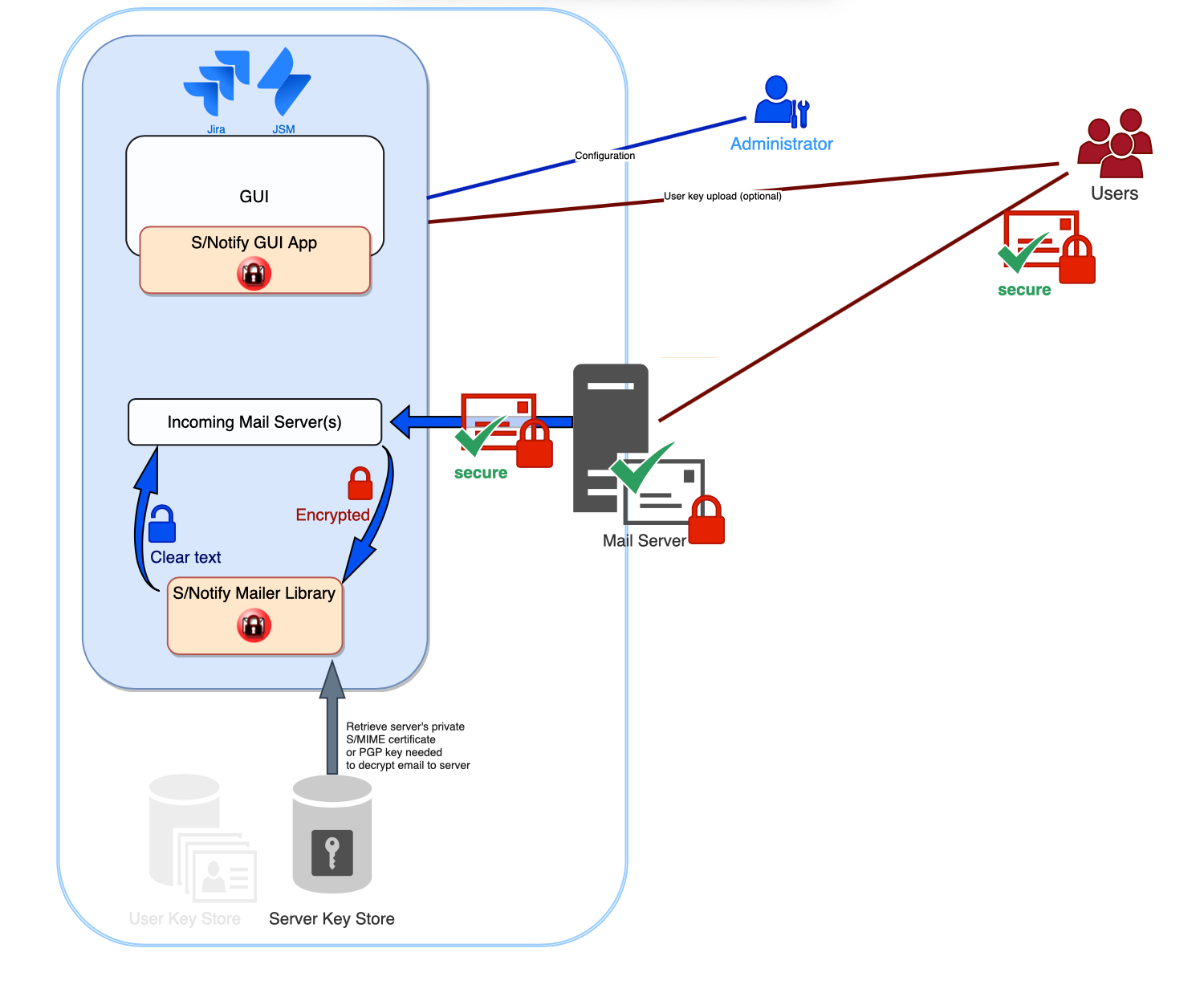
In addition to the email decryption, any S/MIME certificate or PGP key can be extracted to immediately start encrypting any outgoing email to the sender. This allows for automatic encryption setup for enabled users and is particularly useful with Jira Service Management.
